
Effortlessly In Just 2 Weeks!
No more prolonged worry for businesses.
Let us handle it efficiently, saving you time and money.
Here’s how we’ll guide you through the process:
1.Our expert team conducts a quick gap analysis for you (<1 Day)
2.We provide guidance during the implementation phase
3.We ensure you’re well-prepared for compliance (<1 Day)
4.We facilitate both internal and external audits (<1 Day)
5.Simplify Policy & Manage Risk | Audit with Ease
6.Streamline Compliance with Confidence
Submit your details for Fast-Track Compliance!
We have more!
Regulatory & Compliance
Regulatory & Compliance
In today’s business landscape, Governance, Risk, and Compliance (GRC) are crucial for addressing challenges. With emerging laws and regulations, organizations must prioritize transparency, objectivity, and operational excellence. Executives must enforce strict adherence to governance standards, implementing robust compliance systems to mitigate liabilities and maintain stakeholder trust. Proactive GRC strategies, including risk assessments, effective controls, and transparent reporting, are essential for ethical decision-making and long-term sustainability in the face of evolving regulations. GRC serves as the linchpin for organizational excellence, risk mitigation, and compliance assurance.
Your Benefits at a Glance
ISO 27001 Certification
KSA Personal Data Protection Law
KSA Data Management
KSA NCA
UAE Personal Data Protection Law
Abu Dhabi Government Data Management Standards (ADDA)
SOC 1 and 2
PCI-DSS v4.0
Information Assurance Standards
SAMA CSF
SAMA ITGF
ADHICS

The Department of Health (DOH) established the Abu Dhabi Healthcare Information and Cyber Security (ADHICS) Standard. Adoption of the ADHICS Standard by DOH-regulated healthcare entities will better prepare and enable the Abu Dhabi Health Sector to safeguard privacy and security. Its adoption strengthens the government’s efforts to improve security and public confidence through the Health Information Exchange (HIE).
Gap Analysis & Risk Assessment
Risk Treatment Plan
ADHICS Policies & Procedures
Technology Implementation
Security Awareness & Training
Control Check & Audit

ISO 27001

The significance of information security cannot be overstated in today’s digital landscape, and the ISO 27001 certification serves as a beacon of excellence in this regard. At Mast Consulting Group, we understand the critical importance of achieving ISO 27001 certification and the profound impact it can have on your organization’s security posture.
We are committed to partnering with healthcare organizations on their journey towards ISO 27001 compliance. Our comprehensive approach includes:
Gap Analysis & Risk Assessment
Risk Treatment Plan
ADHICS Policies & Procedures
Technology Implementation
Security Awareness & Training
Control Check & Audit

Fast Track Compliance In Days
Whether you are an early stage startup or established organization we will help you in compliance with our automated solution in process.
ISO 20000

ISO 20000 is a framework to identify and manage the key processes involved in delivering effective IT services which meet the needs of the business and the customer. ISO 20000 provides the IT organization with a set of coherent service management processes and a quality management system to manage the full-service lifecycle of an IT service from the end-user’s perspective.
BENEFITS OF ISO/IEC 20000:2011 ITSM IN UAE:
- ISO/IEC 20000 is fully compatible with the ITIL (IT Infrastructure Library) best practice guidance framework for ITSM processes.
- IT service providers become more adaptable to business-led rather than technology-driven services.
- External service providers can utilize certification as differentiation and win new business as it becomes more of a contractual necessity.
- Allows you to identify and manage external service providers.
- More opportunities to improve the efficiency, reliability and consistency of IT services impacting costs and service.
- Certification audits allow for the frequent review of service management processes, which aids in the maintenance and improvement of effectiveness.

PCI DSS
PCI DSS, established in 2004 by major credit card companies, including Visa and MasterCard, is a security standard overseen by the PCI Security Standards Council (PCI SSC).
Although lacking legal enforcement, compliance is mandatory for businesses handling credit or debit card transactions. PCI certification, vital for data protection, not only fulfills a mandatory requirement but is also viewed as the optimal approach to building lasting, trusting relationships with customers.
MAST offers comprehensive support, assisting with PCI DSS assessments, implementation, and certification, including team training. The certification process involves adhering to PCI SSC-established requirements, incorporating well-known best practices for secure card transactions and data protection.

BCMS

Our expertise lies in tailoring Business Continuity Management Systems (BCMS) to diverse organizations across industries. Whether large or small, we craft bespoke programs that align with your unique requirements.
We understand the intricacies of safeguarding operations against disruptions. Secure Link collaborates with you to build a fortified program that ensures uninterrupted operations, instills stakeholder confidence, and fortifies your business against unforeseen challenges.

Lets Connect With Us
Just send us your questions or concerns by starting a new case and we will give you the help you need.
SAMA
With the SAMA Cyber Security Framework, we assist customers in improving their cyber resilience. The Saudi Arabian Monetary Authority (SAMA) has taken on the task of improving cyber resilience by implementing industry best practices, standards, and other frameworks, resulting in the SAMA Cyber Security Framework.
SAMA required entities from all sectors to comply with the Cyber Security Framework and thereby meet the minimal levels of security compliance criteria that will allow them to handle and withstand cyber security threats.
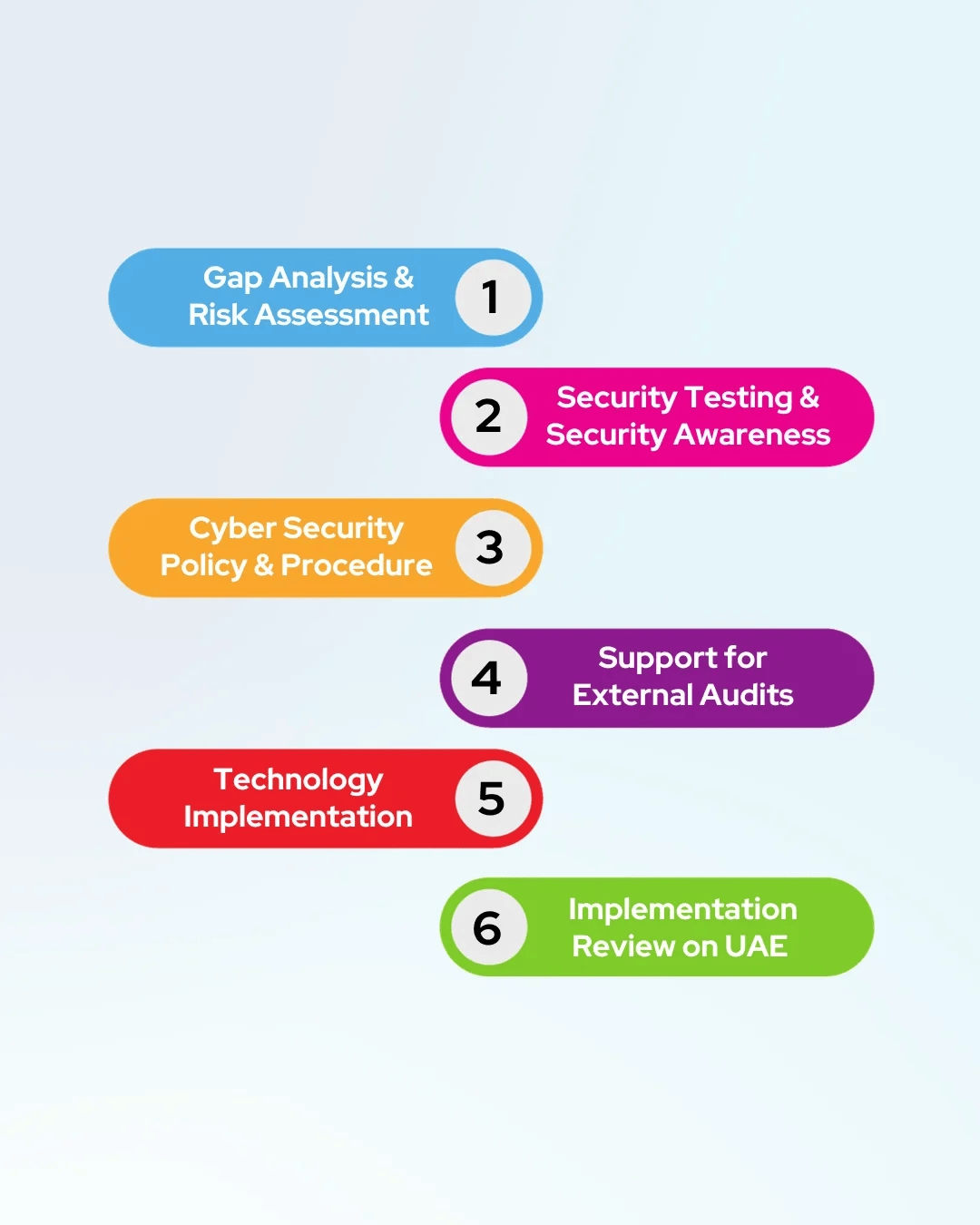
Gap Analysis & Risk Assessment
Risk Treatment Plan
ADHICS Policies & Procedures
Technology Implementation
Security Awareness & Training
Control Check & Audit

UAE IA/ NESA
The UAE Information Assurance (UAE IA ) Regulation (also known as NESA) are critical element of the National Cyber Security Strategy (NCSS) .
The UAE IA Regulation aims to provides a benchmark when capturing and measuring an entity’s Cyber Security Maturity. Such an approach allows actionable decisions to be made while taking under consideration applicability, priority, and status. Consequently, the well-thought structure and depth across both the Management and the Technical controls act as the enabler for continuous improvement towards a well-defined Cyber Resiliency, which can be reflected at a national level if/when needed.
The UAE IA assessment is a collection of fifteen (15) information security domains which are grouped under management (6) and technical controls (9).
The fifteen (15) domains have in total 188 security controls of which sixty 60 controls fall under Management and 128 controls fall under Technical. In addition, each security control has a priority assigned to it which shifts the weight of the outcome allowing to shift the focus and effort towards what matters most. Most importantly, there are thirty-five (35) management controls which are classified as “always applicable”, while the remaining controls are dependent on the outcome of Risk Assessment.


